Given the ever-increasing concerns over data security, there’s a growing interest in the options for data encryption. But encryption isn’t new. Looking back at history, we can find that one of the most notable machines for encryption was Enigma, a machine used in World War II. Going back even further, we find the Caesar cipher, used by Julius Caesar to encrypt messages.
Essentially, encryption involves hiding a message inside another message that usually contains gibberish words. Today, in our digital world, you can see encryption being used in many different areas, such in our browsers, our file systems, emails etc.
Encryption can be a bit difficult in the beginning, especially to non-technical people. But encrypting information is a concern for everybody, and not just people in tech-related fields. (Consider investigative journalists, for example, for whom data protection can be critical.)
In this article, I’ll review a tool that makes encryption easy, and I’ll demonstrate how to send an encrypted text message.
Introducing Keybase
Keybase is an open-source platform for encryption that works as a social network. It tries to make encryption easier, breaking down the barrier of technology and adding a social aspect to it. You can start encrypting by just using a social media username.
On Keybase, you can look up people and follow them just like on Twitter. Keybase also maps your identify to your public key: you can link your other social accounts such as Reddit, GitHub, Twitter to your Keybase profile.
Keybase offers encryption via a web-based client, but also offers local, command-line clients for all major operating systems.
Getting and Setting up an Account
At the time of writing this article, Keybase is still in its alpha phase, and you need an invitation to get an account there. (I do have invitations, so ping me on Twitter if you’re interested.) You can also sign up via the form, but there is a queue, so you may need to wait a while.
Quick tip: You may find a lot of people sending invites on Twitter.
Setting up Your Profile
Once you have got an account on Keybase, you should create your profile. Then head over to the downloads page. Keybase supports all three major operating systems, and there’s also source code. Follow the installation instructions for your operating system.
Once you’ve done that, you can run Keybase:
run_keybase

Yay, we got a squirrel. This confirms we have Keybase ready to encrypt.
Verifying your profiles
Keybase also tries to build this “web of trust” platform by linking your accounts to your Keybase profile. Since Keybase also offers a command line application, I’ll use that to verify my profile later, but you can also use the web version.
Encryption with Keybase
The key part of Keybase is encryption. You can encrypt your message through the Keybase web platform:
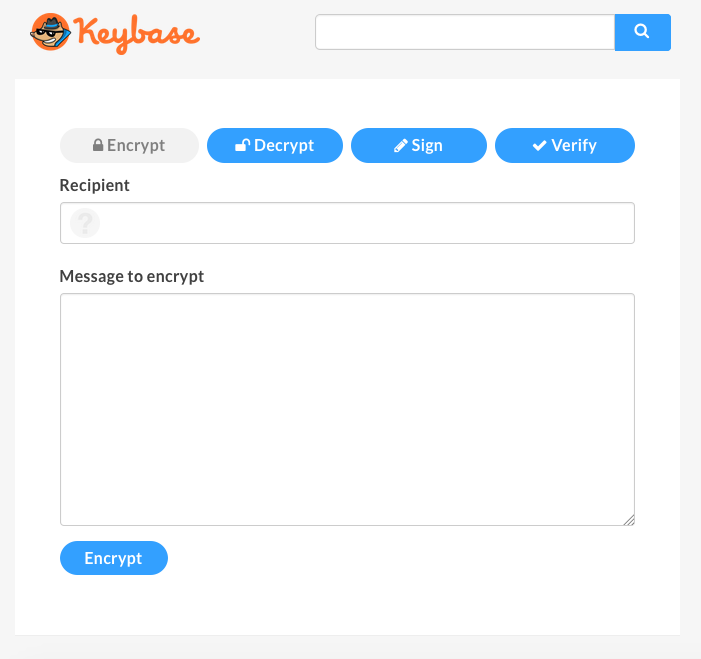
If it’s your first time encrypting information, and you don’t have PGP key, Keybase can generate keys for you.
Click on add a PGP key.
To generate a key, we need to use the open-source application provided by Keybase:
keybase pgp gen # if you need a PGP key
keybase pgp select # if you already have one in GPG
keybase pgp import # to pull from stdin or a file
You can easily generate a key, or import one.
If you’ve chosen to generate a key, it will ask for a public name and email addresses. After entering your information, it will ask if you want to push a copy of the encrypted secret key to the keybase.io servers. This part is optional, but if you want to sign your message (proving that the message is from you) or decrypt them directly from the web application, you’ll have to add it.
First, we need to add the recipient of the encrypted message. Here is one of the features of Keybase. In traditional PGP encryption, you have to look for the person’s key, depending where the person shares their key (personal website, email, public key repositories etc.), then download the person’s key. Keybase offers a very nice search option that looks for the person’s key in Keybase’s database.
Let’s encrypt this message: “Hello from SitePoint”.
It can take a couple of seconds, and it will output the encrypted text:
-----BEGIN PGP MESSAGE-----
Version: Keybase OpenPGP v2.0.58
Comment: https://keybase.io/crypto
wcBMA8DAFbM+aWj3AQgAqhi1b5LPqWrGGKNszk2frmxrLIA7ByXXQu2CP79nnukg
YW1bHEZvkLAxE1T2vYr5T20f/tc3m3JVwLbP0nVO2oKmXjBlNfTh9o1hCLWrYZ3V
NeWMIZyP+k5nHV/oD6v3BuQJWg9ItWAXFuruMXpgXAw4j2uuD4nwJCHPiCyp6+F7
P6yhv5FAiUs63jp5Zy/LsO5wMa58ERwGSqylDzlVMwirvG2mN1VifsgnIQ8DkkyF
f/9VfdX8bnO6hNq0ilB3ZxMhJZ75VvP1CfVuQHrCPH43XTL1enico++6ikeQZ7t/
+MlJpwDrnCQ4+bNknehxD8CrZ8BQu97wgJ+oYkgyKdJQAYSKBunDIy013KgRHMz0
M2hYkqgkmzz/1rDxZSZrNfpRSuTJln3HFfhG9zoKh/hOmvv3bhJUIIKHRnxHT4n6
bDucHUHJntQGmI4zn54lepk=
=b3yA
-----END PGP MESSAGE-----
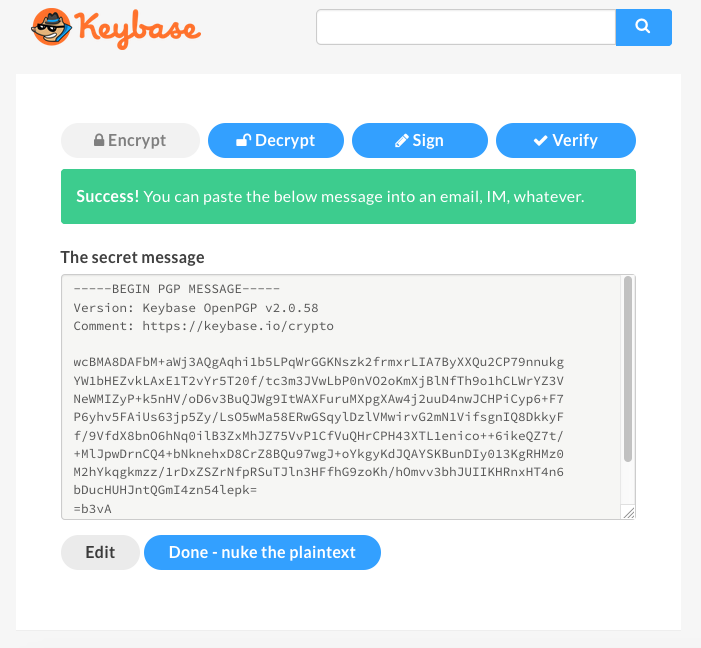
This message can be sent now via email or any other communication platform, and the only person who can see (decrypt) it is the recipient. Nobody else can read or understand this message even if they have access to our emails.
Decryption with Keybase
Click on the Decrypt button and paste your encrypted message. You’ll also need to type your Keybase passphrase. Click Decrypt.
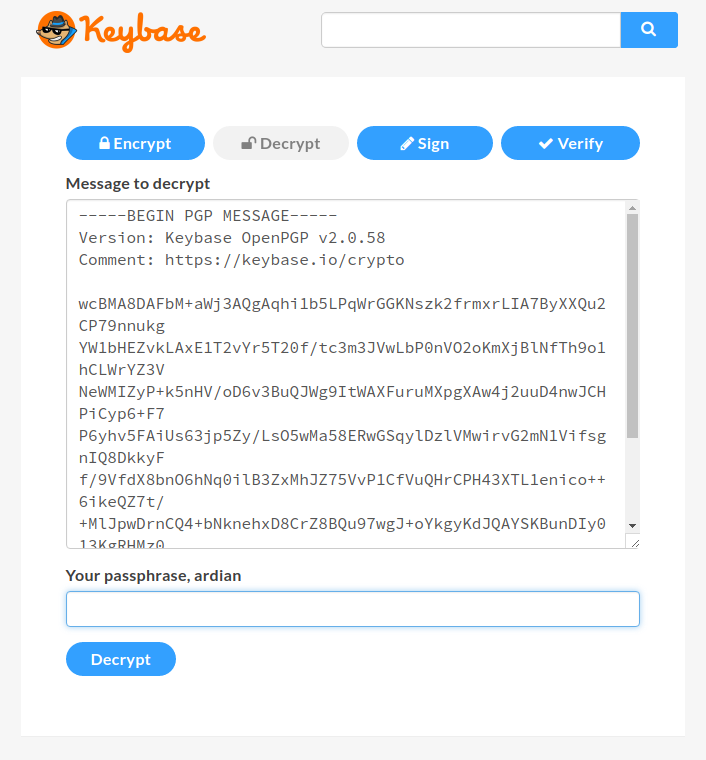
It can take some seconds to decrypt the message, and it will output the original text “Hello from SitePoint”.
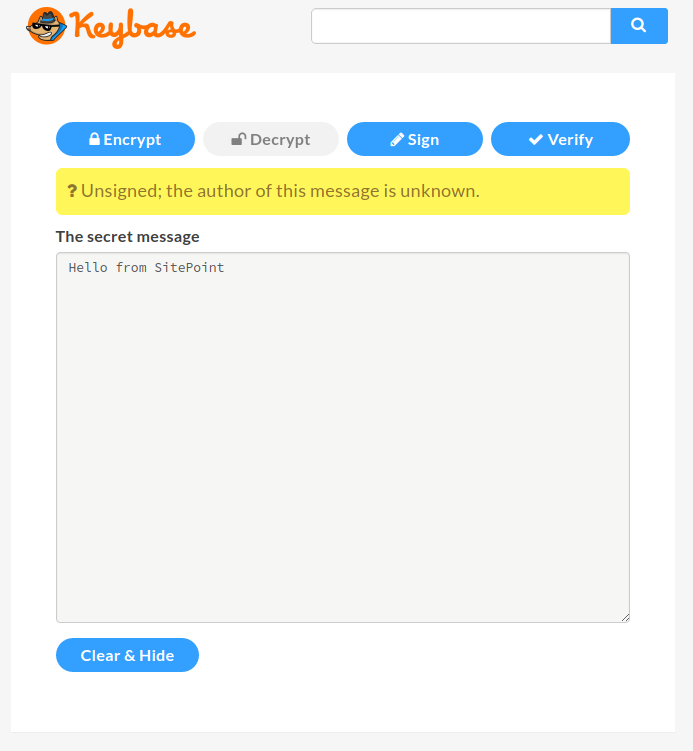
You might notice that, above the secret message, there’s a question mark complaining that the author of the message is unknown. That means the author hasn’t signed the message with their key, and therefore we don’t know the sender. If you want to prove your identify, you should sign your keys. This time, besides adding our message, we’ll also need to put our Keybase passphrase to sign our message (This only works if you’ve added the private key to the keybase.io servers).
-----BEGIN PGP MESSAGE-----
Version: Keybase OpenPGP v2.0.58
Comment: https://keybase.io/crypto
wcBMA8DAFbM+aWj3AQf/aW1VBnvBnxqd0KpIbU9aNcU0Ywz1RvUNaPoutYnrB6JA
CGb85UERiY4GGUFcmlJY6IfJBouBumbVh//3SzzsnnEq/Tq0F3yj0hHu2afx+fxC
lV9P1VketP+XRXCu4vY8SImdcfuIHtYEPFRHiUraNyHn0ZWeN1JfkwePYB3ntgEb
⋮
ohoRqrf7ydFf9ximOcCm4caQO8vBlf/mSj9V2fHRt+1C9o21himN2V2Xl3OvqcrZ
KP3EX/MCu+dAxXG6r3K2gCiL7MD9Ie5ziyWkUb8uDE8jeh7LWWEw9PjBlnZaIrI8
yJbpRhdB49qgvo35d7BhXu1fuZgJlY36DYLbm7nHOg==
=jIRP
-----END PGP MESSAGE-----
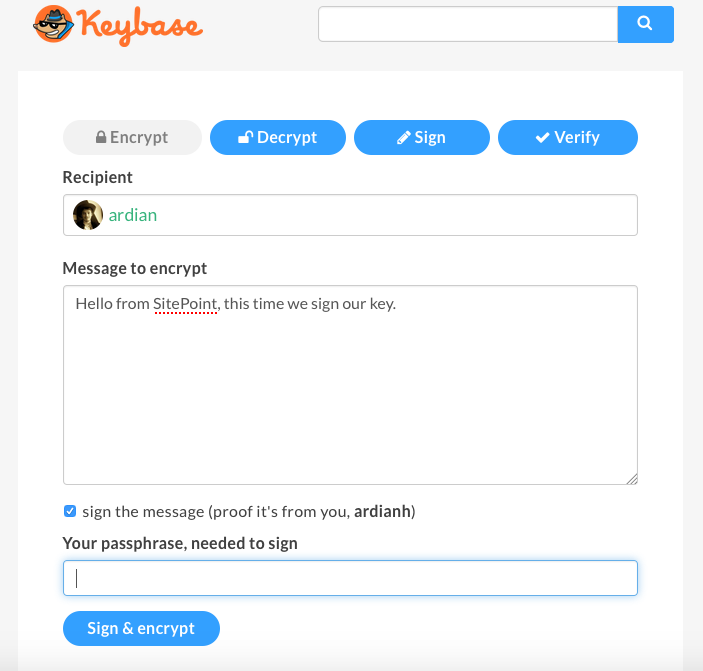
It pretty much looks the same. Now let’s decrypt this message:
Note: I am using two accounts here.
Let’s view our decrypted text now:
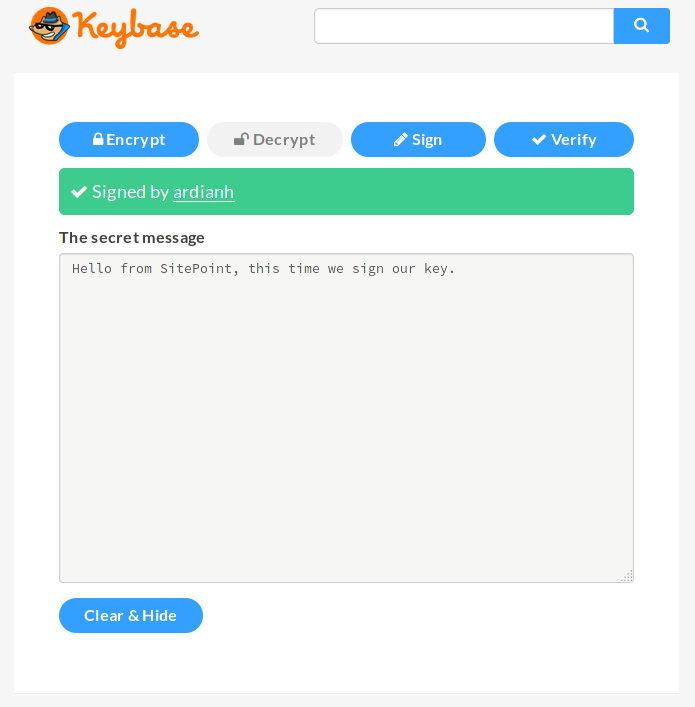
Now we can see our message is signed by user ardianh.
Keybase Command Line App
Now let’s try the Keybase command line application. With the Keybase app installed on your system, you can run run_keybase to verify that it’s installed.
Your first step is to log in to Keybase with keybase login:
1. [computer] macbook-pro
2. [computer] ubuntu-digitalocean-vps
3. [paper key] crunch lyrics
4. I don't have access to any of these devices.
Enter your Keybase username or email address. Then you have to provision your device. If you’ve already logged in via another machine and have access to it, you can use that machine to do the provision. Another option is to use the paper key (which you initially get when you sign up at keybase.io). If you don’t have access to either those, you can still use your Keybase passphrase.
You’ll see something like this:
Enter a public name for this device: digitalocea-vps
✔ Success! You provisioned your device digitalocea-vps.
Now that you’re logged in, the magic can start. I’ll first prove (verify) my Twitter account.
keybase prove twitter
This will ask you to tweet a specific tweet that’s connected with your Keybase username. It’s nice that this process doesn’t require any oAuth authorization from Twitter. You get an email from Keybase letting you know that the identify proof has succeeded. If you were to go to my profile, you’d see that my Twitter profile is added, and you can even view the tweet. The process of linking other social accounts to your Keybase account is mostly the same, and Keybase provides instructions for each of them.
You also don’t have to go to Keybase’s website to encrypt your messages. They can be done directly from the command line application.
keybase pgp encrypt username -m "Hello from SitePoint"`
If you don’t follow the person you’re sending a message to, it will give you information on the username so you don’t pick the wrong person:
▶ INFO Identifying recipient ardian
✔ "ardian" on github: https://gist.github.com/61fed84ba846d4b9055e150818c69e7f [cached 2016-10-27 13:34:33 UTC]
✔ "ardianhaxha" on twitter: https://twitter.com/ardianhaxha/status/782818852442873860 [cached 2016-10-27 13:34:33 UTC]
Is this the ardian you wanted? [Y/n]
-----BEGIN PGP MESSAGE-----
Comment: https://keybase.io/download
Version: Keybase Go 1.0.17 (linux)
wcFMAydk+tkSN8tFARAAgnJZ8YcsqLuIC9FJ9rwXYbrTHMZQo5HWFiltNp/Vue+i
ctptzdBqjuEnCCeonrRunfYTKXgUcB/Aa5edTe84ujyqRaZtrQKwCfSqgKZt9Hyf
q5G8d9jTG/6mKAcUXN2DlErX8FMeUt4HfyNBC4Eq7LAVPdCZW6QsLWZDgbh7jlcO
⋮
Kk4fU13kExGs9zbIIuQ1/Gx0lc3ZUo8zau3XeKtwhFH0n1MgVBE+wNe6o8HJ4tLg
AeSLQdU0tgm370Awi5Y7WFbi4UST4JDg0+E6VeAD4rbLtZPgCuSc6AsauN/BVynG
/fWuKmvC4LfiZvhw2+BB5OSpwUb7tnFgCnLK+wIVUIXih/oQ/uH5KwA=
=i9kE
-----END PGP MESSAGE-----
Keybase will now output the encrypted message. Likewise, decryption can also be done from the command line.
keybase pgp decrypt -i encrypted-message.txt
Hello from SitePoint
The command line application has many more functionalities. Use keybase help to get the list of all the available options.
Conclusion
Keybase has turned encryption into an easy and friendly option for newcomers.
The Keybase team has recently launched a new service called Keybase filesystem, a special place where you can store and share encrypted data. Every user has 10GB of space, and the file system comes installed with the Keybase application.
So, what do you think? Is this something you would use? Have you tried it already? If so, what did you think? Feel free to discuss or ask any questions below.
Frequently Asked Questions (FAQs) about Keybase
How can I ensure my Keybase messages are encrypted?
Keybase automatically encrypts all messages sent through its platform. This means that only the intended recipient, who has the corresponding private key, can decrypt and read the message. The encryption process is seamless and doesn’t require any additional steps from the user. However, it’s important to keep your private key secure to prevent unauthorized access to your messages.
What should I do if I lose my Keybase private key?
If you lose your private key, unfortunately, there’s no way to recover it. This is a security feature designed to protect your messages. If you lose your private key, you’ll need to create a new Keybase account and generate a new key pair. Remember to store your private key in a secure location to prevent loss.
Can I use Keybase to send encrypted files?
Yes, Keybase supports the sending of encrypted files. Just like messages, files sent through Keybase are automatically encrypted. The recipient can then decrypt the file using their private key. This feature makes Keybase a great tool for sharing sensitive documents securely.
How can I decrypt a message or file received through Keybase?
To decrypt a message or file, you’ll need your private key. Keybase automatically decrypts messages and files when you open them. If you’re having trouble decrypting a message or file, make sure you’re using the correct private key.
Can I use Keybase on multiple devices?
Yes, Keybase supports multiple devices. You can install the Keybase app on your computer, smartphone, or tablet and access your account from any of these devices. However, remember that each device will need its own copy of your private key to decrypt messages and files.
Is Keybase secure?
Keybase uses end-to-end encryption, which is currently one of the most secure encryption methods available. This means that only the sender and the recipient can read the messages – not even Keybase can access them. However, the security of your messages also depends on how well you protect your private key.
Can I use Keybase for group chats?
Yes, Keybase supports group chats. You can create a team on Keybase and invite other users to join. All messages sent in the team chat are encrypted, ensuring secure communication within the group.
How can I verify a user’s identity on Keybase?
Keybase provides several methods for verifying a user’s identity. Users can link their Keybase account to their social media profiles, such as Twitter or GitHub. You can check these links to verify a user’s identity.
What happens if I forget my Keybase password?
If you forget your Keybase password, you can reset it using your email address. However, if you also lose access to your email account, you’ll need to create a new Keybase account.
Can I use Keybase without installing the app?
Yes, Keybase offers a web version that you can use without installing the app. However, for the best experience and full functionality, it’s recommended to use the Keybase app.
Ardian is a web developer with a focus on building data-driven back-end APIs. He is very engaged with open source communities such as the Fedora Project and Mozilla.