Cybercriminals have long realized the potential of ransomware and have started to rely on readily available free code to encrypt data on the victim’s computer, such as the open source GnuPG privacy program.
Operators of ransomware VaultCrypt started their business in Russia, but according to recent reports, the malware has reached English-speaking parts of the world, giving trouble to system admins.
Files used for encryption overwritten 16 times
The threat is not as complex in nature as its infamous siblings CryptoLocker or CryptoWall, but this does not make it any less dangerous.
The fact that a ransom alert is not displayed until one of the encrypted files is launched might make it seem rudimentary, but it uses a strong 1024-bit RSA key pair for encryption and deletes the shadow copies of the files to prevent recovery.
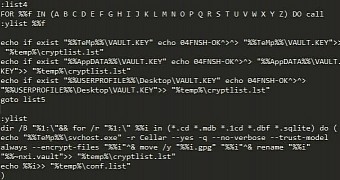
The cybercriminals running VaultCrypt used some interesting methods to achieve their goal, according to an analysis from Bleeping Computer.
It appears that apart from GnuPG, the malware relies on a suite of VBS scripts, all wrapped up in a large Windows batch file, and Microsoft’s sDelete application to remove the data used during the encryption process, and runs 16 overwrite routines.
Private key is encrypted in a file
According to the research, VaultCrypt exports the decryption key in a “vaultkey.vlt” file, which also contains information about the infected computer that is used for personalizing the ransom page and to provide a percentage of the amount of data locked.
The vault key is then encrypted with a master public key that works for all compromised systems. The resulting file is saved locally with the name “VAULT.KEY,” with the private decryption key remaining with the attackers at all times.
The main script powering the malware is publicly available online and it has been tracked down on Pastebin by Fabian Wosar, security researcher at Emsisoft.
Infostealer is also pushed on the infected computer
As if encrypting the data was not enough, it appears that VaultCrypt downloads from a domain hidden in TOR anonymous network another malware with the name “ssl.exe,” whose purpose is to collect log-in credentials from websites visited by the victim.
The command and control (C&C) server is also located in Tor and access to it is protected by a log-in window.
Registration is based on the VAULT.KEY file, which needs to be uploaded in order to receive a user ID and a password. This is the only way the user can find out the ransom amount (about 1 bitcoin) and how it can be paid. The text is mostly in Russian, but some pages contain links to English instructions on Pastebin.
There's a chance to recover files without paying
As is the case with most malware of the same feather, the ransom increases, but it does not double up, after a certain period of time, and the crooks offer the possibility to test the decryption process on four files.
Users impacted by VaultCrypt are not completely without hope, as the threat does not securely delete the encrypted data, leaving the door ajar for recovering the files using free software.
However, this procedure is not guaranteed and restoration from a proper backup file is the safest way to avoid losing data (XLS, DOC, PDF, RTF, PSD, DWG, CDR, CD, MDB, 1CD, DBF, SQLITE, JPG and ZIP) or paying the ransom.
 14 DAY TRIAL //
14 DAY TRIAL //